Published
- 18 min read
Frequently asked Splunk Interview Questions (2024) Part 2
Most commonly asked Splunk interview questions (Part 2/2).
Introduction
This blog post is part 2 of the 2-part series on Splunk Interview Questions. Please find the first part here: Splunk Interview Questions
3.3 How do you detect and respond to security incidents using Splunk?
1. Data Ingestion and Normalization
- Data Collection:
- The first step in detecting and responding to security incidents is to collect the relevant data sources within Splunk. Ingested data might include logs from firewalls, intrusion detection systems (IDS), network traffic data, antivirus software, endpoint detection and response (EDR) tools, and other security devices.
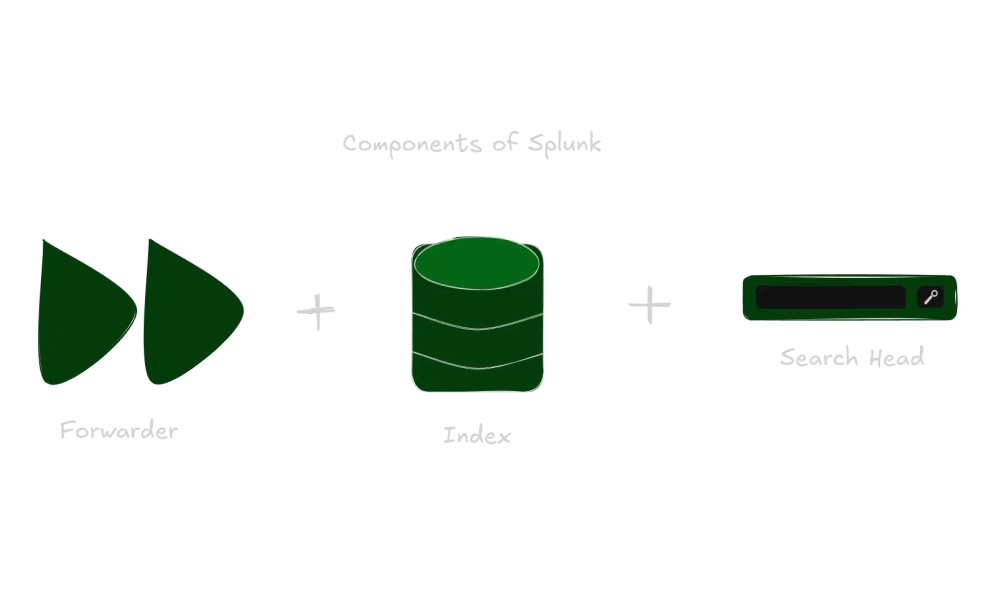
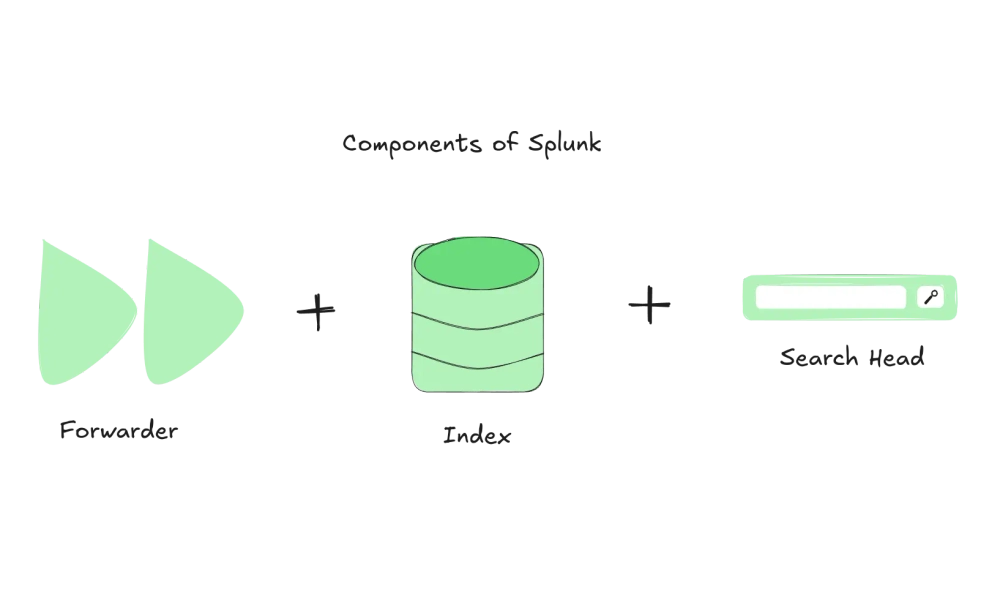
- Use Splunk forwarders to collect and forward data from various sources to the Splunk indexers.
- Data Normalization:
- Use the Common Information Model (CIM) to normalize data from different sources. Modelling ensures consistency and makes searching and correlating data across various sources easier.
2. Threat Detection
- Search and Monitoring:
- Create searches and dashboards to monitor for suspicious activities and anomalies. Use Splunk’s Search Processing Language (SPL) to develop queries to identify potential security incidents.
- Example SPL query to detect failed login attempts:
index=auth sourcetype=access_combined action=failed | stats count by user
- Correlation Searches:
- Use correlation searches to identify patterns and relationships between events that may indicate a security incident.
- Example: Correlate failed login attempts with subsequent successful logins from different IP addresses.
- Alerts:
- Set up real-time alerts to notify security teams of potential security incidents. Configure alerts to trigger based on specific search results or threshold breaches.
- Example: Create an alert to notify the security team if there are more than 10 failed login attempts from a single IP address within an hour.
3. Incident Response
- Incident Investigation:
- Use Splunk’s investigation capabilities to drill down into the details of a potential security incident. Analyze the relevant events, logs, and contextual information to understand the scope and impact of the incident.
- Example: Investigate the source IP address, user accounts, and affected systems involved in a suspected brute-force attack.
- Incident Containment:
- Take immediate action to contain the incident and prevent further damage. Actions may involve isolating affected systems, blocking malicious IP addresses, or deactivating compromised user accounts.
- Example: Use Splunk to generate a list of affected systems and IP addresses, then use network security tools to block or isolate them.
- Incident Eradication:
- Remove any malicious artefacts or unauthorized access from the affected systems. This operation may involve cleaning infected systems, patching vulnerabilities, or restoring systems from backups.
- Example: Use Splunk to identify and remove malware from infected systems and patch all systems to the latest security updates.
- Incident Recovery:
- Restore normal operations and ensure that all affected systems return to normal. Confirm that the team has fully resolved the incident and verify that no threats remain.
- Example: Use Splunk to monitor the affected systems for any signs of recurring issues and validate that all systems are operating normally.
- Post-Incident Analysis:
- Conduct a post-incident analysis to understand the incident’s root cause and identify any lessons learned. Update security policies, procedures, and controls to prevent similar incidents in the future.
- Example: Use Splunk to generate reports and dashboards summarising the incident, its impact, and the actions taken to respond. Analyze the data to identify gaps in security controls and make recommendations for improvements.
4. Automation and Orchestration
- Security Orchestration, Automation, and Response (SOAR):
- Integrate Splunk with SOAR platforms to automate incident response workflows. Use playbooks to automate the detection, investigation, and response to security incidents.
- Example: Use Splunk Phantom to automate the containment and eradication of security incidents based on predefined playbooks.
- Machine Learning and Anomaly Detection:
- Use Splunk’s machine learning capabilities to detect anomalies and potential security incidents—train models to identify unusual patterns or behaviours that may indicate a security threat.
- Example: Use Splunk’s Machine Learning Toolkit (MLTK) to develop models that detect anomalous user behaviour or network traffic patterns.
4. Troubleshooting:
4.1 Can you describe when you had to troubleshoot a performance or functionality issue in Splunk?
You can answer this question based on your personal experience; however, below is the outline for answering this question. Troubleshooting performance or functionality issues in Splunk can involve several steps. Here’s an overview of the process:
- Identify the Symptoms: The first step in troubleshooting a performance or functionality issue is identifying the symptoms. Symptom identification may include slow search times, errors when running reports, high CPU or memory usage, or other problems impacting Splunk’s performance or functionality.
- Reproduce the Issue: Once you have identified the symptoms, reproduce the issue in a controlled environment. Reproducing may involve re-running searches or reports, reviewing logs and configuration files, or performing other diagnostic tests to isolate the root cause of the issue.
- Check Splunk’s Status Page: Before diving into more detailed troubleshooting steps, check Splunk’s status page to see if any known issues or outages may impact your system. You can often find workarounds and updates on the status page if there is a known issue.
- Check System Health: Next, check the health of your Splunk system using the various built-in monitoring tools. Health checks may include reviewing the system dashboards, checking the search head pools, or using other diagnostic tests to identify any hardware, software, or network connectivity issues.
- Check Configuration Settings: Review the configuration settings for your Splunk instance, including data inputs, indexes, and search head configurations. Make sure that these settings are optimized for performance and functionality and adjusted as needed based on best practices and recommendations from Splunk documentation.
- Check Data Quality: Poor quality data can lead to performance or functionality issues in Splunk. Check the quality of your data sources, including log files, network traffic data, and other types of security-related data. Ensure the data is clean, consistent, and properly formatted for indexing and analysis.
- Review Error Messages: Review any error messages or alerts generated during searches or reports. These messages can provide valuable clues about the root cause of the issue, including specific errors, warnings, or exceptions that may be impacting performance or functionality.
- Consult Splunk Documentation and Community: If you are still having trouble troubleshooting the issue, consult Splunk documentation and community resources for additional guidance and support. This activity may include reviewing online tutorials, knowledge base articles, or forums where other users have shared their experiences and solutions to similar issues.
- Engage Splunk Support: If all else fails, engage Splunk’s technical support team for assistance with troubleshooting the issue. Provide detailed information about the symptoms, reproduction steps, and any error messages or logs that may be relevant to the issue. The Splunk support team can help diagnose and resolve complex issues, often through remote access to your system or guided troubleshooting steps.
4.2 How do you approach problem-solving and debugging in Splunk?
1. Understand the Problem
- Define the Issue: Clearly define the problem you are trying to solve or debug. Understand the symptoms, the impact, and the context in which the issue occurs.
- Gather information: Collect all relevant information, including error messages, logs, and any other data that can help you understand the problem.
2. Reproduce the Issue
- Consistent Reproduction: Try to reproduce the issue consistently. This process helps understand the conditions under which the problem occurs and makes diagnosing it easier.
- Isolate the Problem: Narrow down the scope of the problem by isolating the specific components or processes causing the issue.
3. Analyze and Diagnose
- Use Splunk’s Monitoring Tools: Utilize Splunk’s built-in monitoring and diagnostic tools to gather data and insights.
- Search Job Inspector: Analyze the performance and execution details of searches using the Search Job Inspector.
- Monitoring Console: Use the Monitoring Console to check the health and performance of your Splunk environment.
- Splunk on Splunk (SOS): Enable the SOS app to collect diagnostic data and analyze Splunk’s internal processes.
- Review Logs and Alerts: Check Splunk’s internal logs (e.g.,
splunkd.log,search.log) for error messages, warnings, and other relevant information. Review alerts and dashboards for any indications of issues.
4. Formulate Hypotheses
- Identify Potential Causes: Based on the data and insights gathered, formulate hypotheses about the potential causes of the problem. Consider factors such as configuration issues, data quality, performance bottlenecks, and external dependencies.
5. Test and Validate
- Test Hypotheses: Design and execute tests to validate your hypotheses. Make controlled changes to the configuration, data, or environment to see if the issue is resolved.
- Use Debugging Commands: Utilize Splunk’s debugging commands and tools to gather more detailed information. For example, use the
| restcommand to interact with Splunk’s REST API and retrieve diagnostic information.
6. Implement Solutions
- Apply Fixes: Based on the validated hypotheses, implement the necessary fixes or changes to resolve the issue. Applying fixes could involve adjusting configurations, optimizing searches, or updating data ingestion settings.
- Document Changes: Document all changes made during debugging. Documentation helps track the steps taken and helps retain the knowledge for future reference.
7. Verify and Monitor
- Verify Resolution: After implementing the fixes, verify that the issue is resolved by reproducing the scenario and ensuring the problem no longer occurs.
- Monitor for Recurrence: Continuously monitor the environment to ensure the issue does not recur. Use Splunk’s monitoring and alerting capabilities to detect any similar problems in the future.
8. Review and Learn
- Post-Mortem Analysis: Conduct a post-mortem analysis to understand the root cause of the issue, the steps taken to resolve it, and any lessons learned.
- Update Documentation: Update any relevant documentation, runbooks, or knowledge base articles with the insights gained from the problem-solving process.
Common Debugging Techniques in Splunk
- Search Optimization: Optimize searches using efficient search commands, filtering data early, and avoiding resource-intensive operations.
- Data Normalization: Ensure data is normalized and indexed correctly to improve search performance and accuracy.
- Configuration Management: Regularly review and optimize Splunk’s configuration settings to ensure optimal performance and functionality.
- Use of Diagnostic Tools: Leverage Splunk’s diagnostic tools and commands to gather detailed information and insights during debugging.
4.3 What are some common errors or issues you encountered in Splunk, and how did you resolve them?
You can answer this question based on your experience working with Splunk. Here are the most common errors that one can face in Splunk.
1. Data Quality Issues
- Symptoms: Data not parsing correctly, missing fields, or incorrect timestamps.
- Causes: Incorrect configuration of source types, props.conf, or transforms.conf files.
- Resolution:
- Ensure the source types are correctly defined, as well as the props.conf and transforms.conf files are configured properly.
- Use the Data Quality dashboard in the Splunk Monitoring Console to identify and fix data quality issues.
- Test data ingestion in a development environment before deploying to production.
2. Search Performance Issues
- Symptoms: Slow search performance, timeouts, or incomplete search results.
- Causes: Inefficient search queries, high data volume, or insufficient resources.
- Resolution:
- Optimize search queries by filtering data early, using efficient search commands, and avoiding wildcards.
- Ensure that the hardware meets Splunk’s IOPS, CPU, and memory requirements.
- Use summary indexing and data model acceleration to improve search performance.
3. High CPU and Memory Usage
- Symptoms: High CPU or memory usage, slow system performance.
- Causes: Resource-intensive searches, insufficient hardware resources, or misconfigured settings.
- Resolution:
- Identify and optimize resource-intensive searches.
- Scale out by adding more search heads or indexers.
- Monitor system performance using tools like vmstat, iostat, and top to identify bottlenecks.
4. Orphaned Objects
- Symptoms: Errors related to orphaned scheduled searches, reports, or alerts.
- Causes: Users who created these objects have left the organization, or their accounts are deactivated.
- Resolution:
- Identify orphaned objects using the Orphaned Scheduled Searches, Reports, or Alerts dashboard.
- Reassign or delete the orphaned objects as needed.
5. Version Compatibility Issues
- Symptoms: Discrepancies in features or functionality between different versions of Splunk components.
- Causes: Mismatched versions between Universal Forwarders (UFs) and Indexers/Search Heads.
- Resolution:
- Ensure that all components are compatible and update UFs when necessary.
- Review the release notes and compatibility matrix before upgrading.
6. No Events Found in Index
- Symptoms: No events are found in the index despite data being ingested.
- Causes: Issues with data ingestion, configuration errors, or communication problems between UFs and Indexers.
- Resolution:
- Check the internal logs (e.g., splunkd.log) for errors or warnings.
- Verify that Splunk can read the directory or file being monitored.
- Ensure there are no communication issues between UFs and Indexers.
7. Time-Based Issues
- Symptoms: Incorrect timestamps, alerts not triggering, or data retention problems.
- Causes: Incorrect timezone settings, timestamp parsing issues, or data aggregation problems.
- Resolution:
- Ensure that the timezone settings are correctly configured.
- Verify that timestamps are being parsed correctly.
- Use the _time and _indextime fields to troubleshoot and resolve time-based issues.
8. General Troubleshooting Tips
- Check Logs: Always check the Splunk internal logs (e.g., splunkd.log) for errors or warnings.
- Use Diagnostic Tools: Utilize Splunk’s diagnostic tools and commands to gather detailed information.
- Monitor System Performance: Regularly monitor system performance using tools like vmstat, iostat, and top.
- Consult Documentation: Refer to Splunk’s official documentation and community resources for additional help and best practices.
5. Best Practices:
5.1 Can you describe your methodology for designing and implementing a Splunk deployment?
Designing and implementing a Splunk deployment involves a structured approach to ensure that the deployment meets the organization’s data ingestion, storage, search, and analysis requirements. Here is a methodology for designing and implementing a Splunk deployment:
1. Requirements Gathering
- Stakeholder Interviews: Conduct interviews with stakeholders to understand their data needs, use cases, and expectations.
- Data Sources Identification: Identify all data sources that need to be ingested into Splunk, including logs, metrics, and other machine data.
- Use Cases Definition: Define the specific use cases for Splunk, such as IT operations, security, business analytics, or compliance.
- Performance and Scalability Requirements: Determine the performance and scalability requirements based on data volume, search frequency, and user load.
2. Architecture Design
- High-Level Architecture: Design a high-level architecture that includes the key components of the Splunk deployment, such as forwarders, indexers, search heads, and deployment servers.
- Data Flow: Define the data flow from data sources to Splunk, including data ingestion, parsing, indexing, and searching.
- Component Sizing: Size the components based on data volume, search load, and performance requirements. Use Splunk’s sizing guidelines and best practices.
- High Availability and Disaster Recovery: Design for high availability and disaster recovery, including component redundancy, data replication, and failover mechanisms.
3. Infrastructure Planning
- Hardware and Software Requirements: Determine the hardware and software requirements for each component, including CPU, memory, storage, and operating system.
- Network Configuration: Plan the network configuration, including network segments, firewall rules, and data encryption.
- Security Considerations: Implement security measures, such as access controls, encryption, and monitoring, to protect the Splunk deployment.
4. Data Ingestion and Parsing
- Data Ingestion Methods: Choose the appropriate data ingestion methods, such as files, network ports, APIs, or databases.
- Data Parsing and Indexing: Configure data parsing and indexing using props.conf and transforms.conf files to ensure that data is correctly parsed and indexed.
- Data Normalization: Use the Common Information Model (CIM) to normalize data from different sources, ensuring consistency and ease of search.
5. Search and Analysis
- Search Head Cluster: Implement a search head cluster to distribute search loads and improve search performance.
- Data Models and Acceleration: Create data models and use data model acceleration to speed up searches and dashboards.
- Knowledge Objects: Define knowledge objects, such as event types, tags, lookups, and field extractions, to enrich and categorize data.
6. Monitoring and Alerting
- Monitoring: Implement monitoring to track the health and performance of the Splunk deployment, including component health, data ingestion rates, and search performance.
- Alerting: Configure alerts to notify administrators and users of critical events, performance issues, or security incidents.
7. Access Control and User Management
- Role-Based Access Control (RBAC): Implement RBAC to control access to data and functionality based on user roles and permissions.
- User Management: Manage users and roles using Splunk’s user management features, including integration with external authentication systems like LDAP or SAML.
8. Deployment and Configuration
- Installation: Install Splunk components on the planned infrastructure, following the architecture design and sizing guidelines.
- Configuration: Configure Splunk components, including data inputs, outputs, indexes, and search settings.
- Validation: Validate the deployment by testing data ingestion, search performance, and functionality against the defined use cases.
9. Documentation and Training
- Documentation: Document the Splunk deployment, including architecture, configuration, use cases, and troubleshooting guides.
- Training: Train administrators, users, and stakeholders to ensure they understand how to use and manage the Splunk deployment.
10. Continuous Improvement
- Monitoring and Optimization: Continuously monitor the Splunk deployment and optimize performance, scalability, and functionality based on usage patterns and feedback.
- Updates and Upgrades: Regularly update and upgrade Splunk components to benefit from new features, security patches, and performance improvements.
5.2 How do you ensure data quality and accuracy in Splunk?
Ensuring data quality and accuracy in Splunk involves several key steps. Here are some best practices to follow:
- Define Data Quality Standards: Define clear standards for data quality and accuracy, including acceptable levels of completeness, consistency, and accuracy. These standards should be aligned with the specific use case or business problem that Splunk is being used to address.
- Establish Data Validation Rules: Establish validation rules to ensure that incoming data meets the defined standards for data quality and accuracy. This may involve configuring data inputs, field extractions, and other settings in Splunk to filter out or correct invalid or corrupt data.
- Monitor Data Quality Metrics: Monitor data quality metrics continuously to identify trends, patterns, and anomalies that may indicate data quality or accuracy issues. This may involve tracking metrics such as data volume, completeness, consistency, and accuracy over time.
- Implement Data Cleaning Techniques: Implement data cleaning techniques to correct errors, inconsistencies, and other issues with incoming data. This may involve using features in Splunk, such as the “eval” command or “lookups” to transform, enrich, or modify data as it is ingested into Splunk.
- Test Data Quality Periodically: Test data quality periodically by comparing incoming data to expected values or reference data sets. This may involve using features in Splunk such as the “validate” command or “stats” command to compare and analyze data samples.
- Implement Data Governance Policies: Implement data governance policies to ensure that data is collected, stored, and managed in a consistent and controlled manner. This may involve defining roles and responsibilities for data management, establishing data access controls, and implementing data security policies.
- Provide Training and Support: Provide training and support to users to ensure that they are using Splunk correctly and following the best practices for data quality and accuracy. This may involve providing documentation, tutorials, or other resources to help users understand how to configure and use Splunk properly.
- Continuously Monitor and Improve: Monitor and improve data quality and accuracy over time by implementing new features, tools, or techniques as needed. This may involve upgrading to newer versions of Splunk, implementing new apps or add-ons, or modifying existing configurations to optimize performance and reliability.
5.3 What are some best practices for managing and maintaining a Splunk environment?
1. Capacity Planning and Scaling
- Capacity Planning: Regularly assess your data volume, search load, and user requirements to plan for future capacity needs. Use Splunk’s capacity planning tools and guidelines to estimate resource requirements.
- Scaling: Scale your Splunk environment horizontally by adding more indexers, search heads, and other components as needed. Ensure that your hardware and infrastructure can support the increased load.
2. Performance Monitoring
- Monitoring Console: Use the Splunk Monitoring Console to monitor the health and performance of your Splunk environment. Track key metrics such as CPU usage, memory usage, disk I/O, and search performance.
- Alerts and Notifications: Set up alerts and notifications to proactively monitor and respond to performance issues, errors, and other critical events.
3. Data Management
- Data Retention Policies: Implement data retention policies to manage the lifecycle of your data. Define retention periods for different data types and configure Splunk to automatically archive or delete old data.
- Data Model Acceleration: Use data model acceleration to speed up searches and dashboards. Create and accelerate data models to improve search performance and reduce resource usage.
4. Index Management
- Index Optimization: Optimize your indexes by configuring index settings such as thawed and frozen periods, bloom filters, and TSIDX settings. Ensure that your indexes are configured for optimal performance and storage efficiency.
- Index Archiving: Archive old indexes to reduce storage usage and improve search performance. Use Splunk’s index archiving features to move old data to secondary or cold storage.
5. Search Optimization
- Efficient Searches: Optimize your searches by using efficient search commands, filtering data early, and avoiding resource-intensive operations. Use the Search Job Inspector to analyze and optimize search performance.
- Concurrent Searches: Limit the number of concurrent searches to prevent resource contention and ensure optimal performance. Configure the maximum number of concurrent searches in the
limits.conffile.
6. Security and Compliance
- Role-Based Access Control (RBAC): Implement RBAC to control access to data and functionality based on user roles and permissions. Ensure that only authorized users have access to sensitive data and critical functions.
- Audit and Compliance: Use Splunk’s audit and compliance features to monitor and enforce compliance with internal policies and external regulations. Track user activities, data access, and configuration changes.
7. Backup and Disaster Recovery
- Regular Backups: Perform regular backups of your Splunk configuration, data, and indexes. Use Splunk’s backup and restore features to ensure that you can recover from data loss or system failures.
- Disaster Recovery Planning: Develop and test a disaster recovery plan to ensure business continuity in case of a major outage or failure. Configure Splunk for high availability and failover to minimize downtime.
8. Updates and Upgrades
- Regular Updates: Keep your Splunk environment up-to-date with the latest patches and security fixes. Regularly update Splunk components to benefit from new features, performance improvements, and security enhancements.
- Upgrade Planning: Plan and test upgrades carefully to ensure compatibility and minimize disruption. Use Splunk’s upgrade guidelines and best practices to ensure a smooth upgrade process.
9. Documentation and Training
- Comprehensive Documentation: Maintain comprehensive documentation of your Splunk environment, including architecture, configuration, use cases, and troubleshooting guides. Document all changes and updates to ensure knowledge retention and continuity.
- User Training: Regularly training administrators, users, and stakeholders to ensure they understand how to use and manage the Splunk environment effectively. Offer training on new features, best practices, and troubleshooting techniques.
10. Community and Support
- Community Engagement: Engage with the Splunk community through forums, user groups, and events. Share knowledge, ask questions, and stay updated on the latest trends and best practices.
- Support Contracts: Consider purchasing Splunk support contracts to ensure access to technical support, professional services, and expert guidance.